The long-awaited Ethereum merge has been scheduled, and I’m sure by now you have seen dozens of articles about all the possibilities and outcomes of the merge. Assuming everything is successful, We take a close look into why we should be concerned about replay attacks post Ethereum Merge.
Introduction to “Replay attacks”

With the merge, two chains will now be present, PoW and PoS. This will create two versions of your NFTs and assets.
Wouldn’t It make sense to sell it on the old chain to get them all out the Ethereum? This is the primary issue that leaves you subjected to a replay attack.
This is basically where a transaction that happens on one chain can be exploited to happen on another. For example, you decide to list your BAYC NFT on the PoW chain, hoping to cash out and still have a copy to hold and show it off.
The issue however is that an individual could “replay” the transaction on Ethereum 2.0. Selling your BAYC on the new chain, leaving you will nothing.
What exactly are “Replay Attacks”?
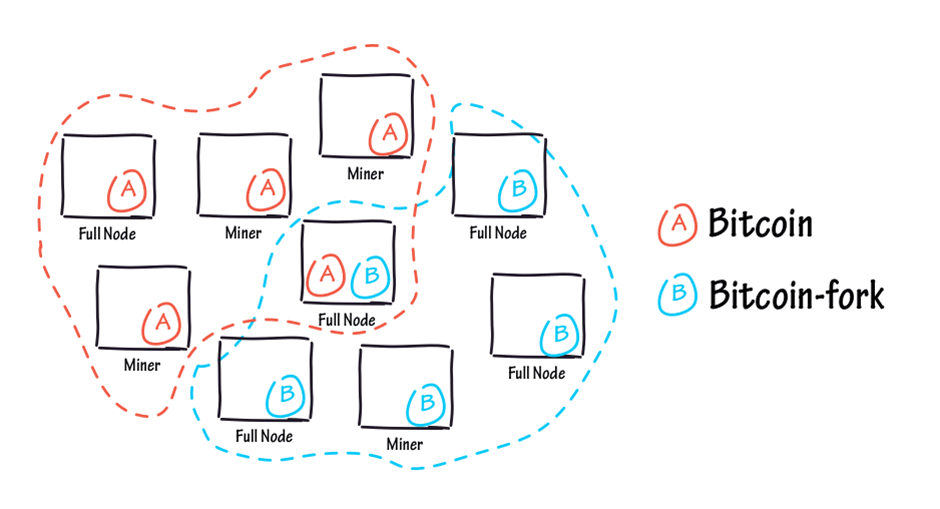
Traditionally, a replay attack happens when a malicious figure sneaks up on a secure network connection and intercepts it, resulting in them being able to delay or resend another data transaction to subvert the receiver.
As these messages are intercepted from a network, there is no need to decrypt them, effectively defeating the cryptography aspect of crypto networks.
In financial institutions, attackers use it to duplicate transactions so that they can take money out of accounts. Some cybercriminals may also choose to modify some parts of the message to obtain valuable information, also known as a cut-and-paste attack.
In the blockchain context, replay attacks can occur significantly during hard forks, such as the Ethereum 2.0. Hard forks are basically where an existing ledger is divided into two, usually one with legacy software and the other with the divided version (ETH 2.0 Context). However, they can also be used to create new cryptocurrencies.
During these forks, entities can use replay attacks as well. This is because any transaction made by a person whose access was valid before the hard fork is also made on the Eth PoS chain.
This also means that the transaction made bypasses blockchain security by duplicating the transaction and having the same identical unit on another account (e.g. hackers account).
Cryptography doesn’t work in this case because the PoS chain cannot identify which chain this compromised transaction was for, and this transaction is them validated on the old PoW chain and in the PoS chain, making you lose your assets.
Read More
Regarding ETHPoW: An Ethereum hard fork could be on the horizon.
— olimpio ⚡️ (@OlimpioCrypto) August 11, 2022
Yesterday a made a thread on what it could mean.
This is a follow-up:
(i) what is a hard fork
(ii) risks of interacting with a forked chain
(iii) what happens with L2s?
(iv) why would a hard fork happen?
🧵👇
How do we prevent them?
I tried to find a way of using both the POS / POW chains, after the $ETH #Merge, that's 100% safe vs. replay attacks.
— Elerium115 (@elerium115) August 13, 2022
I would appreciate any (in)validation, from anyone more knowledgeable!
1) Before the merge, send assets from your main wallet "A", to a temporary wallet "B"… pic.twitter.com/20PvBDxfZY
As highlighted by @elerium115 on Twitter, this is a possible model to be 100% safe from replay attacks. It would be good to send assets from your main wallet (A) to a temporary wallet (B). It would also be good to prepare another wallet (C) for the PoW chain before the merge.
After the merge, the assets from wallet B can be sent to wallet A for the PoS chain and the assets from wallet B can be sent to wallet C on the PoW chain. This would break the connection and allow you to mess around with the PoS chain safely.
Replay attacks cannot happen as the chain is broken but take note that wallet A should not be used on PoW and wallet C should not be used on PoS.
TLDR
Before the merge: Delist any NFTs you may have for sale
After the merge: Transfer your NFTs and ETH on the PoW chain to a new wallet. This would break the link between your assets. Furthermore, this should be relatively inexpensive.
The replay attack can be applied to any sort of fungible and non-fungible asset. The best case doesn’t interact with the PoW chain at all to prevent this situation from happening. Hopefully, this would prevent you degens from selling your ETH PoW assets immediately after the merge.
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
Featured Image Credit: Chain Debrief
Also Read: Is Anyone Really Winning The Layer 2 War? Here’s What The Stats Say