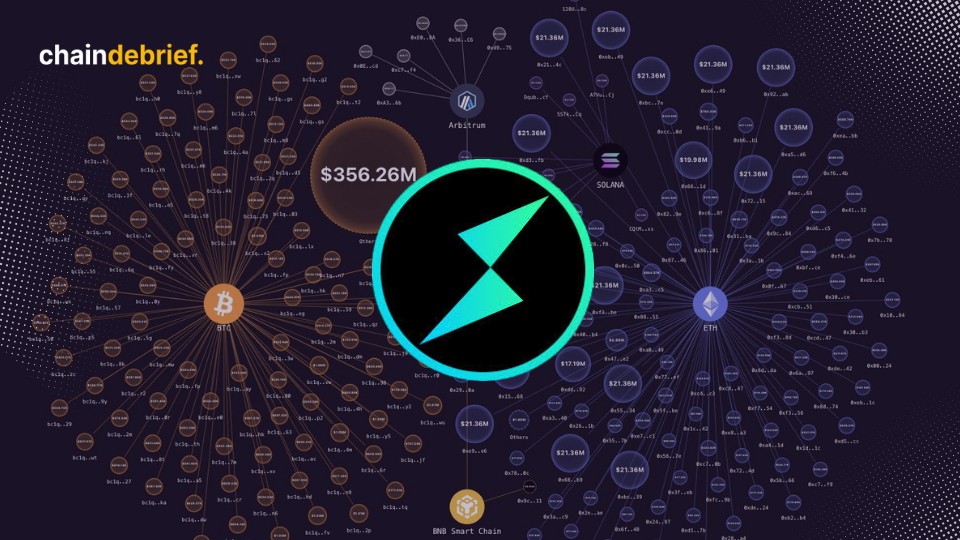
An extraordinary surge in maximum extractable value (MEV) block rewards occurred on Ethereum following a turbulent exploit targeting specific liquidity pools on the decentralized exchange Curve Finance.
As a result of an issue in Vyper compiler in versions 0.2.15-0.3.0, following pools were hacked:
— Curve Finance (@CurveFinance) July 31, 2023
crv/eth
aleth/eth
mseth/eth
peth/eth
Another pool potentially affected is arbitrum’s tricrypto. Auditors and Vyper devs could not find a profitable exploit, but please exit that one
Yesterday witnessed the most lucrative day for MEV since the Merge that took place last year, with approximately 6,006 ETH ($11.1 million) distributed as MEV rewards to validators, according to data from mevboost.pics.
Today has produced some of the largest MEV reward blocks in Ethereum’s history.
— eric.eth (@econoar) July 30, 2023
Slot 6,992,273: 584 ETH
Slot 6,993,342: 345 ETH
Slot 6,992,050: 247 ETH
Slot 6,993,346: 51 ETH
Detailed examination of on-chain data from the Ethereum blockchain highlighted multiple slots that yielded significant MEV rewards.
Notably, slot 6,992,273 recorded a reward of 584 ETH (approximately USD$1m) , slot 6,993,342 offered 345 ETH (~USD$640,000), and slot 6,992,050 closely followed with a reward of 247 ETH (SD$459,000).
These observations were first made by analyst and investor Eric Conner, also known as Eric.eth on Twitter,and all three events occurred within the past 24 hours. These figures bear importance, considering that the average MEV payment per block stands at about USD$100, or 0.06 ether per block.
White Hat MEV Operator Saves Curve $5.4m
On-Chain MEV Operator c0ffeebabe.eth managed to front-run any potential exploits on the affected curve pool, just moments before any other malicious transactions were able to fully drain the CRV-ETH pool.
there is hope, the babes are communicating pic.twitter.com/XoCixmOhWD
— banteg (@bantg) July 30, 2023
The white hat hacker managed to front-run a malicious hacker, saving 2,879 ETH, or approximately USD$5.4m in the process, and later returning it to the curve deployer address.
#PeckShieldAlert There are $26.76M exploited so far from @AlchemixFi, @JPEGd_69, @MetronomeDAO, @DebridgeFinance and @Ellipsisfi pic.twitter.com/SXGG9m9Nww
— PeckShieldAlert (@PeckShieldAlert) July 30, 2023
However, approximately USD$52 million in funds were still stolen from Curve in multiple other attacks, affecting the treasuries of protocols such as MetronomeDAO and JPEGd.
While a full post-mortem has yet to be published, security audit firm PeckShield has notified users that the vulnerability laid in reentrancy issues in Curve’s smart contract code due to using an outdated version of the Vyper programming langugage.
Reentrancy exploits allow malicious users to “call” the same function multiple times, such as multiple illicit withdrawals above the appropriate threshold.
Also Read: 30 Crypto Hacks Over $30M, Broken Down
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
Featured Image Credit: Chain Debrief