Heard of the Forbes 30 under 30?
Well, we’re not so lucky in crypto. In fact, the only one to make it on that list was SBF – and we all know how that turned out (Hint: he made this list too!).
Unfortunately, an overarching theme surrounding crypto has been exploits, and with more than $3 Billion this year alone, it may be time to aggregate them, and see if we can learn something, if anything at all.
Huge thanks to Rekt for tracking the top exploits and hacks throughout crypto, alongside breaking down what happened.
Also Read: I Asked OpenAI 22 Questions About Blockchain, Here Are The Answers
30. Grim Finance – $30 Million
Teetering on the edge of making the list, Grim Finance was exploited for $30 million late in 2021.
The Fantom-native yield optimizer, which was a fork of popular project Beefy Finance, was the victim of a “reentrancy” vulnerability In essence, the attacker was able to withdraw more than their initial deposit amounts by using flash loans.
5) So what was the big mistake of grim finance?
— Rugdoc.io (@RugDocIO) December 18, 2021
1. No reentrancy guard on a pattern that absolutely needs it (@0xPaladinSec always points this out)
2. Giving the user more privilege than is necessary: There is absolutely no need for the user to be able to choose the deposit token
Despite Grim Finance having been previously audited by Solidity Finance, a DeFi audit firm, the exploit passed undetected. The firm subsequently informed that the audit had been done by “an analyst who was new to the team” and that the vulnerability was not caught during peer review.
29. Spartan Protocol – $30.5 Million
One of the first Binance-Smart Chain (BSC) based protocols to be exploited by a flash loan, Spartan Protocol lost over $30.5 million in a May 2021 attack.
The protocol, which aimed to be an innovative DeFi platform for all, was using an altered version of the UniswapV2 code. However, this alteration also allowed an attacker to remove more liquidity than they had provided from various pools.
By amplifying the damage with flash loans and repeating the attack multiple times, they were able to drain most of the liquidity from the targeted pools.
Spartan Pools v1 exploited – team are aware and investigating.
— Spartan Protocol (@SpartanProtocol) May 2, 2021
Spartan Protocol had not been audited prior to the exploit.
28. Meerkat Finance – $32 Million
Occurring shortly after the Spartan Protocol Hack, Meerkat Finance was another BSC-native project that suffered a major exploit.
BSC project Meerkat Finance is suspected of being rug, taking away 13.96 million BUSD, and the other 73,635 BNB. MKAT claimed to be hacked and stole all resources. Currently the project website cannot be opened. This may be the largest fraud project on the binance smart chain. pic.twitter.com/KbdclfDBKA
— Wu Blockchain (@WuBlockchain) March 4, 2021
According to an investigation by Rekt, Meerkat Finance’s code allowed the owner to withdraw assets from various vaults at any time. Essentially, the team had a backdoor that could be accessed at any point of time.
While the team claimed that it was a hack, they quickly deleted their social media accounts afterwards, and ghosted users.
It was therefore likely that this was a rug pull done by insiders, unless there was solid evidence that their private keys had been compromised.
Meerkat Finance had not been audited prior to the exploit.
27. Vee Finance – $34 Million
In late 2021, Vee Finance, an Avalanche-based lending protocol, was exploited during one of the most bullish phases in Avalanche history.
Announcement: Our platform may have been exploited. All services have been paused. We are investigating the cause, please follow our official accounts for latest update.
— vee.finance🔺 (@VeeFinance) September 20, 2021
Thanks!
Funding his Ethereum address via Tornado Cash, the exploiter then bridged to Avalanche, and created trading pairs for the pools he intended to attack.
Despite failing during his first two attempts due to insufficient gas fees, the third eventually succeeded.
The exploit involved both oracle manipulation as well as taking advantage their oracle not processing for decimals.

While Vee Finance had previously been audited by both Slowmist and Certik, Vee Finance apparently ignored some pressing issues in their code.
26. Alpha Homora – $38 Million
In what was the biggest DeFi hack at the time, the multi-chain lending and yield farming platform Alpha Homora were exploited for $37.5 million overnight.
What made this exploit different, however, was the trail of evidence pointing to the whole fiasco being an inside job. The exploit also did not affect user funds, but those between Alpha Homora and Ironbank ($CREAM), in a “protocol-to-protocol” lending way.
yeah, but the attacker's contract (fake spell) used Alpha Homora's access to Iron Bank to borrow the funds.
— vasa (@vasa_develop) February 13, 2021
It's like using a fake company (Alpha Homora) credit card to bill all your expenses on their account.
In essence, the attacker needed to know a list of information only privy to those working on Alpha Homora V2 at the time, performing multiple transactions in order to borrow an infinite amount of assets from Ironbank.
While Alpha Homora had previously been audited by both Quantstamp and Peckshield, the insider knowledge required means that they hacks could have occurred despite a thorough audit.
25. Kucoin – $45 Million
In 2020, the KuCoin exchange was hacked, resulting in the loss of $150 million worth of various cryptocurrencies.
The hack was carried out by a group of unknown attackers, and KuCoin was criticized for its inadequate security measures, and several investigators estimated the true value of the exploited funds to be closer to $280 million.
However, several protocols swiftly worked to mitigate the damage by forking, freezing, or blacklisting the stolen funds.
⚠️ $VELO tokens affected in KuCoin’s security breach from the wallet below will be invalidated and frozen.
— Velo Official (@veloprotocol) September 26, 2020
GBM3PJWNB5VKNOFXCDTTNXPMUNBMYTLAAPYDIIKLHUGMKX7ZGN2FNGFU
Please do NOT transact on any Stellar-based DEXs until this issue has been resolved and announced.
Thank you. pic.twitter.com/RsA18TeLow
While Kucoin performed their own internal audits, the hacker did remove funds via access to the Kucoin hot wallet private key, and not brute force – which may hint towards another inside job.
24. PancakeBunny – $45 Million
Another exploit that happened on BSC, Pancake Bunny is a DeFi yield aggregator used for popular BSC based Decentralized Exchange PancakeSwap.
Unfortunately, their code included an exploit that allowed the attacker to manipulate the price of their native token $BUNNY.
To do so, the attacker took several flash loans depositing them into pools, and claiming over 6.97 million $BUNNY, valued at $1 billion at the time.
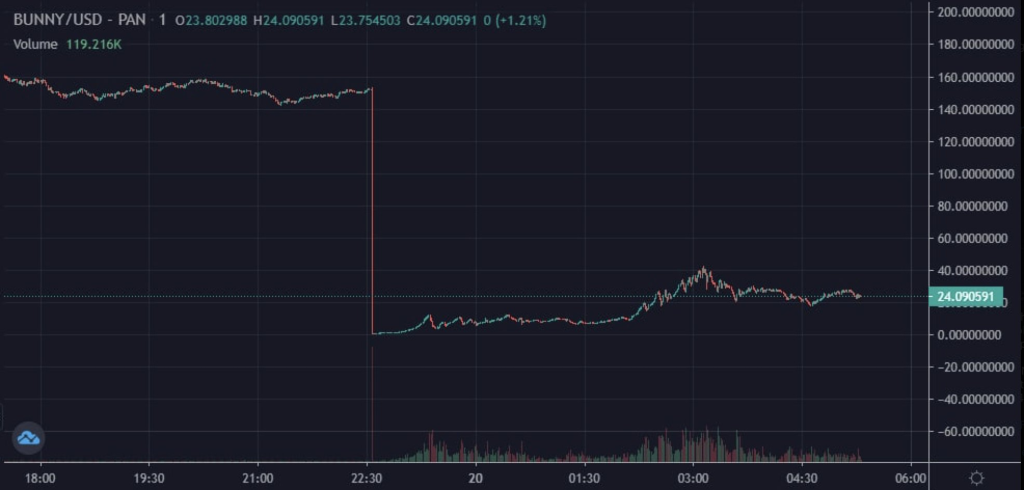
This caused the price of $BUNNY to immediately plunge over 94% instantly as the attacker sold the tokens.
Just a few months later, PancakeBunny also suffered an exploit on the Polygon Chain, and has since not recovered.
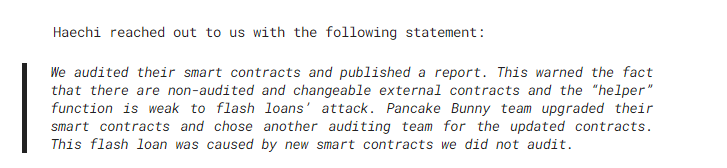
While the protocol was initially audited by Haechi, they released a follow-up statement, stating that the affected smart contracts were not audited by them as PancakeBunny had switched auditors prior to publishing them.
23. Cashio – $48 Million
Our first Solana entry, Cashio, a stablecoin protocol allowed users to mint $CASH which was pegged to $1, using various tokens as collateral.
Please do not mint any CASH. There is an infinite mint glitch.
— Cashio ($CASH) 💵 (@CashioApp) March 23, 2022
We are investigating the issue and we believe we have found the root cause. Please withdraw your funds from pools. We will publish a postmortem ASAP.
However, the attacker found an exploit that allowed him to mint an unlimited amount of $CASH. By creating multiple fake accounts to pass validation checks, he could use his own token as collateral, and minted $2B in the stablecoin.
While the attacker eventually refunded some funds for accounts with less than $100K, they made away with almost all of Cashio’s TVL.
Cashio had not been audited prior to the exploit.
22. bZx – $55 Million
bZx, a Defi Lending platform, suffered a total of four hacks in 2 years. While 2 of them required more advanced techniques, the nail in the coffin came from a simple phishing email.
This was disguised as a word document, and ran a script on a key developer’s computer that compromised the bZx private keys.
#bZx private key compromised, over $55 million dollars stolen so far. We’ll continue to update as more information is discovered. @RektHQ @ChainNewscom @bZxHQ https://t.co/SM6WWDt06J pic.twitter.com/39S05IiBFr
— SlowMist (@SlowMist_Team) November 5, 2021
Their protocol suffered exploits on both Polygon and BSC simultaneously, and more than $55 Million in user funds had been drained.
bZx had not been audited prior to the exploit.
21. Uranium Finance – $57.2 Million
This BSC-based Uniswap Clone learnt the hard way that “code is law” on the blockchain. While most of their code was copied from other projects, they made a small, but fatal mistake in one line that caused it to implode.
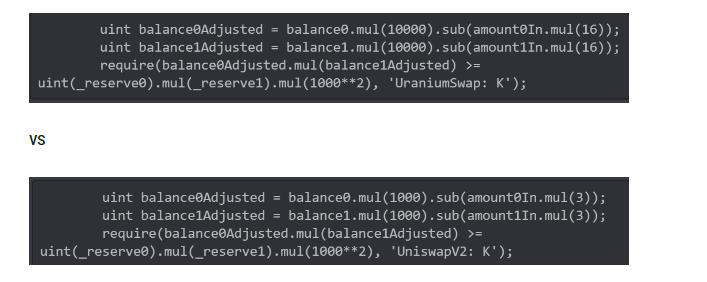
While copying Uniswap’s code, they forgot to change “1000” to “10,000” in the last line, allowing the attacker to withdraw more than deposited from the exchange.
Uranium Finance had not been audited prior to the exploit.
20. EasyFi – $59 Million
One of the first major hacks on the Polygon network had DeFi lending Protocol, EasyFi, as its victim.
Exploited for $6 Million in stablecoins and $53 Million of their native token, $EASY, following which, the attacker held 30% of $EASY’s total supply.
1/3 On Monday, 19th April 2021 our team members reported the transfer of a large amount of EASY and protocol funds from designated contracts & wallets. initial investigation revealed the possibility of compromise of mnemonic phrase.
— Ankitt Gaur (@AnkittGaur) April 19, 2021
The exploit occurred due to EasyFi’s private keys being compromised, and a deeper investigation revealed that user funds were being controlled with a admin key.
No multisig or cold wallet was used.
Easy Finance had not been audited prior to the exploit.
19. Ascendex – $77.7 Million
Centralized exchange Ascendex was one of a list of exchanges that faced exploits last year, to the tune of $77.7 million. These funds were being held in hot wallets across the Ethereum, BSC, and Polygon networks.
In what had to be the “steady lads” of 2021, the exchange promised all users refunds, but went on to halt withdrawals and delete tweets recommending safeguarding private keys.
Ascendex had not been audited prior to the exploit.
18. Qubit Finance – $80 Million
Launched by the team behind PancakeBunny, which appeared at no.24 on this list, Qubit Finance was a DeFi lending protocol which allowed for “Cross-Chain Collateralization”.
However, this also allowed for cross-chain points of failure. An attacker figured out that you were able to borrow against your BSC collateral on Ethereum, without ever having deposited on Ethereum in the first place.
We'd like to offer the exploiter the highest bounty in history.
— Qubit Finance (@QubitFin) January 30, 2022
Let's retweet this! pic.twitter.com/eQ0iUOaxiy
Despite offering the highest “bounty” in crypto at the time the $80M, comprised of wETH, stablecoins, and various Binance-native tokens, were never seen again.
Qubit informed that they had been audited by Theori, a professional auditing firm.
17. Fei Rari – $79.5 Million
The DeFi stablecoin protocol Rari was one of the most exciting projects towards the tail end of DeFi summer, attracting a TVL of over $2 Billion. However, it’s vulnerability lay in code it had forked from Compound.
This code failed allowed reentrancy attacks, and an attacker was able to use flash loans to withdraw multiple times against the same collateral.
A proposal to deprecate Rari Capital governance is live. This is the last necessary action to deprecate all Rari Capital protocols. Tribe delegates can vote here.https://t.co/0MPnsDoMX1
— Rari Capital (@RariCapital) October 13, 2022
Rari was subsequently deprecated, following several attempts to negotiate with the exploiter and revive the protocol.
Rari Capital had not been audited prior to the exploit.
16. Mirror Protocol – $92 Million
Mirror Protocol, a Terra-based platform that allowed you to gain exposure to equities via synthetic assets suffered multiple exploits over a span of 2 years.
The worst part? They didn’t even acknowledge it until Twitter users pointed it out.
🧵👇 What if I told you that Mirror Protocol, up until 18 days ago, was susceptible to the one of the most profitable exploits of all time, allowing an attacker to generate $4.3m from $10k in a single transaction? Here's how I discovered this – by pure serendipity. 🧵👇
— FatMan (@FatManTerra) May 27, 2022
The initial attack occurred in 2021, when an exploiter was able to create duplicate withdrawals, from which $90M was drained from Mirror. The team, however, failed to notice this till 6 months later, and tried to quietly patch things up.
Another attack came following the collapse of Terra and $UST, due to on-chain oracles equating the price of $LUNC to $LUNA2.
It is unclear whether Mirror Protocol was audited following the collapse of $UST.
15. Harmony Bridge – $100 Million
One of the most devastating exploits to date, the Harmony Bridge, was drained for $100 Million, collapsing the entire Harmony ecosystem.
It used a 2 out of 5 multisig, of which 2 addresses were compromised, enough to drain a significant amount of its TVL. While the team quickly updated it to be a 4 out of 5 multisig, it was too little, too late.
1/ The Harmony team has identified a theft occurring this morning on the Horizon bridge amounting to approx. $100MM. We have begun working with national authorities and forensic specialists to identify the culprit and retrieve the stolen funds.
— Harmony 💙 (@harmonyprotocol) June 23, 2022
More 🧵
So all in all, if two of the four multisig signers are compromised, we're going to see another 9 figure hack. Considering all that's been going on lately, it'd be interesting to hear some details from @harmonyprotocol on how these EOAs are secured.
— Ape Dev (@_apedev) April 1, 2022
While we can point fingers at the Harmony team for not listening to warnings and having such lax security around over 9 figures of user funds, the exploit was a major hit to crypto. The blockchain has yet to recover from the exploit.
It is unclear whether the Harmony Bridge was audited prior to the exploit.
14. Mango Markets – $117 Million
Mango Markets, a Solana-based trading protocol, was one of the largest projects building on the network at the time.
However, the attacker this time managed to find an exploit not just in the code of the protocol, but also the liquidity of its native token, $MNGO. By taking out a huge long on $MNGO, the attacker managed to liquidate a massive amount of shorts, pushing its price up by 1,000%.
The attacker also borrowed all of Mango market’s available liquidity using the unrealized profit from the long position, leaving the protocol with over $100 million in bad debt.
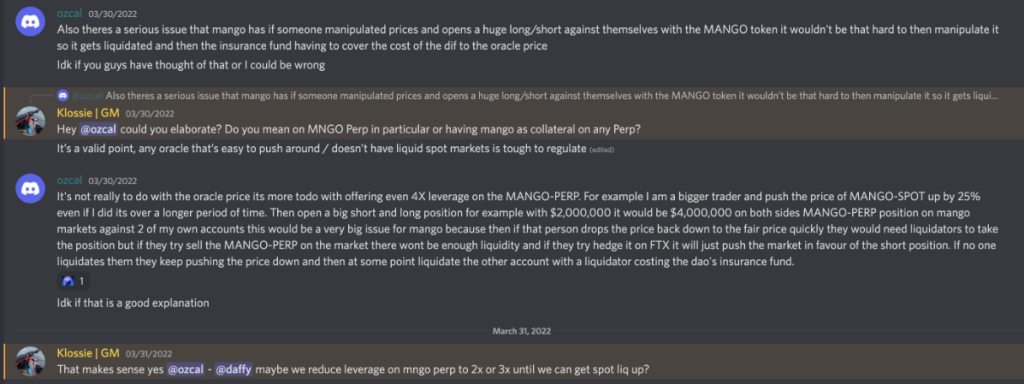
While a user had pointed out the possibility of such an attack prior to the exploit, the issue seemed to never have been fully addressed by the team.
Mango Markets had been audited by Out of Scope prior to the attack.
13. BadgerDAO – $120 Million
Defi Yield platform BadgerDAO was the victim of a front-end exploit in 2021.
While other exploits required flaws in the code, the BadgerDAO exploiter took advantage of a feature instead. “Infinite approvals”, which are generally approved by regular users of protocols, allows an unlimited amount of tokens to be transferred from wallets to smart contracts.
The exploiter took advantage of this, and after gaining access to the API key for BadgerDAO’s frontend, was able to drain user wallets to the tune of $120 million.
So someone on the $BADGER discord flagged the Increase Allowance exploit on the Badger UI a few days ago. Sadly, the team brushed it aside.
— 0xMoves (@0xMoves) December 2, 2021
If your users are saying they're being requested to do things on your platform that seem odd, PLEASE take it seriously. https://t.co/WUYMhU9viz pic.twitter.com/S7VaqJ2DEr
A peculiar fact about this incident was that the front-end was manipulated 12 days prior to the hack, and that a user had actually flagged suspicious activities in their Discord.
BadgerDAO had not been audited prior to the exploit.
12. Cream Finance – $130 Million
Cream Finance, a decentralized lending platform which was part of the Yearn ecosystem ($YFI) was unfortunately the victim of multiple exploits.
The attacker figured out a vulnerability in the system, and used flash loans to repeatedly borrow and lend across two addresses. By doing so, the collateral in his vault appeared to be worth more than it was to the protocol, and the attacker used this to clear Cream’s vaults.
We are investigating an exploit on C.R.E.A.M. v1 on Ethereum and will share updates as soon as they are available.
— Cream Finance 🍦 (@CreamdotFinance) October 27, 2021
Cream Finance had previously been exploited for $18 Million, and had been caught in the crossfire of other multi-million exploits in the past.
Cream Finance had not been audited prior to the exploit.
11. Vulcan Forged – $140 Million
Known for their token $PYR, Vulcan Forged was a blockchain game studio that was building their own metaverse.
To perform in-game transactions, user accounts were linked to an integrated wallet, which was powered by Venly. While users were in the metaverse adventuring, however, an attacker managed to gain access to 96 private keys, draining their funds.
This not include $PYR, but also various other tokens on Ethereum and Polygon.
All those who have had their funds stolen from their Vulcan wallet, please email [email protected] using the email they registered.
— Vulcan Forged (@VulcanForged) December 13, 2021
Include a metamask address to replace your funds.
All development will be allocated to a new decentralized solution.
We’ll recover.
Fortunately for those affected, the stolen $PYR was replaced by the team’s deep treasury, and most users were made whole.
Vulcan Forged had not been audited prior to the exploit.
10. Compound Labs – $147 Million
In one of the most ridiculous entries onto this list, Compound Labs, a crypto yield platform, lost approximately $140 Million in their native $COMP token.
How?
An initial $80M in $COMP were distributed to the wrong addresses due to two typos in the protocol’s code.
Following that, another vault had a vulnerability exposed, where users could claim $COMP regardless of whether they were allocated any. While the team was attempting to patch this issue, users realized the error and drained the relevant vault.
While the CEO of Compound Labs, Robert Leshner, did not shy away from public appearances, his passive-aggressive response to those who took advantage of the error did not help the cause.
While $38.7 Million was returned, this paled compared to the $147 Million stolen.
Compound had not been audited prior to the exploit.
9. Wintermute – $162.3 Million
Market Maker Wintermute’s exploit was one of the largest of 2022, draining approximately $160 Million from various asset pools.
We’ve been hacked for about $160M in our defi operations. Cefi and OTC operations are not affected
— wishful cynic (@EvgenyGaevoy) September 20, 2022
The exploit was initially to a vanity-address used by Wintermute, which the CEO assured was for gas-saving purposes.
The cherry on top was a honeypot scam created by the same exploiter named WinterMuteINU, that managed to siphon almost 166 $ETH away from those trying to capitalize on the event.
Wintermute had not been audited prior to the exploit.
8. Beanstalk – $181 Million
The Beanstalk hack was once again, the result of a “feature”, and now a flaw. Essentially, the attacker was able to use a governance proposal to drain funds from the protocol.
For governance proposals on Beanstalk, there is only a 1 day delay for all governance actions for the contract of its native stablecoin, $BEAN.
Knowing this, the attacker set up two proposals, one to steal all the money in the contract, and the second to send $250,000 in $BEAN to the Ukraine donation funds.
By using a flash loan, the attacker was able to vote a majority “yes” on the proposals, transferring funds from the smart contract to the attacker’s wallet instead.
We’re engaging all efforts to try to move forward. As a decentralized project, we are asking the DeFi community and experts in chain analytics to help us limit the exploiter's ability to withdraw funds via CEXes. If the exploiter is open to a discussion, we are as well. https://t.co/fwceVz6hbi
— Beanstalk Farms (@BeanstalkFarms) April 17, 2022
The attacker then quickly absconded with the funds to Tornado Cash, never to be seen again.
Beanstalk was audited prior to the hack by Omniscia. However, the audit firm pointed out that such an attack “fell outside the scope of their audit”.
7. Nomad Bridge – $190 Million
The Nomad Bridge Hack will go down in crypto history as, ironically, the most decentralized hack.
While the first attack was only for a sum of $2.3 Million, news of the exploit quickly spread, and almost everyone could join in. This led to $190 Million being drained within a matter of hours.
New wave… looks like its still being actively exploited pic.twitter.com/bxMTwOTdZM
— Spreek (@spreekaway) August 1, 2022
Following the first attack, which took advantage of a security flaw in the protocol that read certain messages as valid, users could copy and paste the same function from Etherscan and siphon funds from Nomad.
In fact, 2 addresses got away with almost $100 Million by themselves, with neither being the original exploiter.
Nomad Bridge was audited by Quantstamp, and had flagged some security issues that, evidently, the Nomad team had not sufficiently addressed.
6. BitMart – $196 Million
In another advent of “steady lads”, Centralized Exchange BitMart assured users that any exploits were fake news following rumors circulating that their wallets had been compromised.
However, their CEO eventually confirmed it, suspending withdrawals, and noting that the loss was valued at $150 Million. While the stolen assets were mostly memecoins, the actual valuation at the time hovered closer to $196 Million.
2/4 BitMart will use our own funding to cover the incident and compensate affected users. We are also talking to multiple project teams to confirm the most reasonable solutions such as token swaps. No user assets will be harmed.
— Sheldon Xia (@sheldonbitmart) December 6, 2021
Thankfully, BitMart had sufficient funds to cover the losses experienced. Another statement on their website also stated that less than 0.5% of all user funds were kept in hot wallets.
It is unclear whether BitMart had an external audit prior to the exploit.
5. Wormhole – $326 Million
Wormhole, a bridge that allowed users to transfer funds Solana and other networks, was exploited for a whopping 120,000 $ETH, or $326 Million at the time.
Going down as one of the most notorious hacks in crypto, the exploit left hundreds of millions in tokens unbacked, putting DeFi at serious risk at the time.
holy fucking shit @wormholecrypto is not having a good time right now pic.twitter.com/Q6tcqAngCL
— samczsun (@samczsun) February 2, 2022
While the details of this exploit are extremely technical, I’ll attempt to break it down.
Essentially, the attacker was able to bypass several checks in the bridge, and take advantage of a code discrepancy. This made the smart contracts think that the attacker had more funds in the initial wallet than in reality.
The attacker was then able to fraudulently mint 120K worth of $ETH on the Solana Network, and bridge a majority of it back to Ethereum.
Despite it being one of the largest hacks in crypto history, the team behind wormhole were able to scrounge up the 120K $ETH required at the time to back the on-chain assets.
Wormhole was audited by Neodyme prior to the exploit.
4. SAM BANKMAN-FRIED & FTX – $477 MILLION
As if the collapse of FTX wasn’t bad enough, an attacker came after the funds stuck in the exchange, following withdrawals halting.
1) What
— SBF (@SBF_FTX) November 14, 2022
What indeed.
While it is unclear as to who the perpetrator was, many suspected an insider, and the official FTX statement was that it was due to unauthorized access. Some also speculate that this was done under the instructions of the Securities Commission of The Bahamas.
Either way, the $477 Million was the final blow to FTX, with most users writing off their funds from there on out.
Also, FTX was audited in the metaverse.
3. BNB Bridge – $586 Million
The BNB bridge, which allowed users to move assets between the old Binance Beacon Chain and the BSC, was exploited to the tune of 2 Million $BNB, or approximately $586 Million at the time.
They were able to do this by exploiting a bug in the bridge, allowing them to mint $BNB directly into their wallets.
Instead of swapping directly to stables and attempting to bridge off of Binance, the attacker deposited the $BNB and collateral and attempted to move borrowed funds to other networks. This had huge ramifications on the Binance ecosystem, where entire protocols were drained of liquidity.
Due to irregular activity we're temporarily pausing BSC. We apologize for the inconvenience and will provide further updates here.
— BNB Chain (@BNBCHAIN) October 6, 2022
Thank you for your patience and understanding.
While the chain was eventually halted, approximately $127 Million had already been siphoned by the attacker to other chains. Thankfully, a majority of the funds were either blacklisted by Tether or recovered by the Binance Chain.
Binance was also able to cover the funds lost, thanks to their hefty reserves.
It is unclear whether BNB Bridge had been audited prior to the exploit.
2. Poly Network – $611 Million
In what was the biggest hack at the time, Poly Network, which allowed for cross-chain swaps, was hacked for $611 Million.
That’s more than half a billion. Half a billion dollars, poof, gone, disappeared.
Important Notice:
— Poly Network (@PolyNetwork2) August 10, 2021
We are sorry to announce that #PolyNetwork was attacked on @BinanceChain @ethereum and @0xPolygon Assets had been transferred to hacker's following addresses:
ETH: 0xC8a65Fadf0e0dDAf421F28FEAb69Bf6E2E589963
BSC: 0x0D6e286A7cfD25E0c01fEe9756765D8033B32C71
While no private keys were compromised, what happened was a lot more complicated. Without digging into the technical details, the attacker discovered that they could access a privileged piece of code, from which they could transfer Poly Network’s funds to themselves.
The hacker eventually returned some funds after broadcasting a series of messages. However, this was far from the ~$600 million stolen.
Poly Network was not audited prior to the exploit.
1. Ronin Bridge (Axie Infinity) – $624 Million
THE largest hack to date, the Ronin bridge allowed users to connect from Ethereum to the Ronin Network, which hosted popular P2E game Axie Infinity.
It used a 5 out of 9 validator system to approve deposit and withdrawal contracts, out of which 4 were operated by Sky Mavis, the creators of Axie Infinity.
Furthermore, one of the validators which was operated by Axie DAO, had given control to Sky Mavis for transaction fee optimization. While this was supposed to be a short-term agreement, the approval was never revoked.
By gaining access to Sky Mavis’ keys, they had control of 4 Sky Mavis Validators + 1 Axie DAO validator, giving them the majority vote on the network.
I noticed that Axie bridge was exploited for $600m 6 days ago, so I shorted AXS with high leverage
— Cobie (@cobie) March 29, 2022
I was early. I executed quickly, like the expert traders taught me
Within 24 hours I was liquidated because nobody else noticed the hack for 6 days and the price pumped instead 🙌
Unfortunately, the hack was only realized by the team six days later, and by that time it was too late to halt the bridge.
Ironically, there was a huge short position on a centralized exchange that was placed immediately after the hack. Due to it not being discovered, however, the position got liquiditated.
The team behind the Ronin bridge has since moved to a 8 out of 9 validator system.
The Ronin Bridge was not audited prior to the exploit.
Closing Thoughts
All in all, 11 of the above exploits occurred due to compromised private keys, with the remaining 19 happening because of faulty code.
Furthermore, most of the projects involved were unaudited, or did not address pressing issues in their audits.
In a world where code is law, it becomes tiring to play defense, as developers not only have to work on their project constantly, but also have to keep checking for errors.
After all, the projects only go through their code ever so often, but attackers have an unlimited amount of time to pinpoint a single error, which could net them tens, if not, hundreds of millions of dollars from their computer.
So, where should we go from here? Should we ban flash loans and hide all code repositories?
In a decentralized, permissionless world – that simply cannot be the case. While Vitalik had previously said that the future of crypto is not cross-chain, the number of emerging use cases from new blockchains along with the flow of TVL across networks shows that users are simply not ready to accept that yet.
In the meantime, we may simply have to be more vigilant in our checks, and learn from every multi-million dollar mistake.
Once again, huge thanks to Rekt, without which this list would have been much, much more difficult to source.
Also Read: Here’s What You Can Do After Metamask Updated Its Privacy Policy
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
Featured Image Credit: Chain Debrief