Web 3.0 is one of the biggest innovations the world has seen in recent times. This decentralized online ecosystem is an integration of various new-age concepts, such as blockchain technology, token-based economics, and smart contracts.
Smart contracts are simply self-executing programs that run on the Ethereum Virtual Machine (EVM) – and similar chains – to automate an agreement between a creator and a recipient. A smart contract can be used to drive a token, like Ethereum-based tokens or even non-fungible tokens, or a function within a decentralized application (dApp).
Smart contracts are similar to conventional computer programs, they can be created and deployed by anyone who has the technical know-how. Unfortunately, some malicious individuals try to exploit the decentralized nature of Web3 and take advantage of unsuspecting smart contract users.
For this reason, it is critical to learn about the potential risks of smart contracts and the things to look out for when signing Web3 transactions. In this article, we will be discussing how not to fall victim to various smart contract risks.
Also Read: USE These 6 Tips To Never Get Caught in a Crypto Pump and Dump Again
1. Download A Security Extension
One of the most efficient ways of protecting yourself when transacting on Web3 is via security extensions or tools.
These software suites or plugins enable users to perform a variety of actions on their crypto wallet, while enhancing their online security. Crypto wallets are essential components for interacting with smart contracts.
Don’t forget that we have our own Open Edition!
— Fire (@_joinfire) January 30, 2023
Immediately test out the Fire extension by minting a FREE Fire Card that gives you access to our Discord server!
🔥 pic.twitter.com/asfKUcAnpo
Some wallet security tools are designed to preview what will enter and exit your wallet before you sign a transaction. Meanwhile, other security extensions will ensure your digital assets are safe each time you perform an on-chain transaction. Certain wallet security tools even go as far as intercepting malicious transactions before they process on the network.
Some of the top security tools to consider for your smart contract transactions include Fire, Kevlar, Pocket Universe, Blowfish, etc. Installing one of these security extensions can help protect you from malicious sites and projects.
2. Be Wary Of Approval Scams
Approval means giving a smart contract the authorization to interact with a specific token, in a particular amount, and when they require. By giving approval to a smart contract, you would be handing the decision-making power over your assets to a computer program, which could have been developed by anyone.
btw Merlin is a 100% rug,
— yieldfarming (@delucinator) April 26, 2023
It approves uint256 max to feesto address (deployer) which let it get drained
LP tokens can be withdrawn but liq can't be removed for the same reason, there are no funds left in the pool
Source: @overnight_fi team member pic.twitter.com/QyZJZwCrPx
For example, if you authorize a dApp’s access to a token, you will be giving it control over a certain quantity – or perhaps all – of that token in your wallet. You need to be very careful when signing these smart contract authorizations, as one could easily fall victim to a token approval scam.
Before approving any smart contract’s access to your assets, there are certain questions you need to ask yourself. You should ask if the token being requested is relevant to the dApp function you intend to use. Also, check if the amount of token being requested makes logical sense.
3. Confirm Smart Contract’s Address On Relevant Block Explorer
Every – or at least a reputable – smart contract has a verifiable address. Whether a token, an NFT collection, or a dApp, a legitimate smart-contract-driven project will ensure its address is readily available – either on its main site or in docs. Hot wallets, like Metamask, also display a smart contract’s address before you sign any transaction.
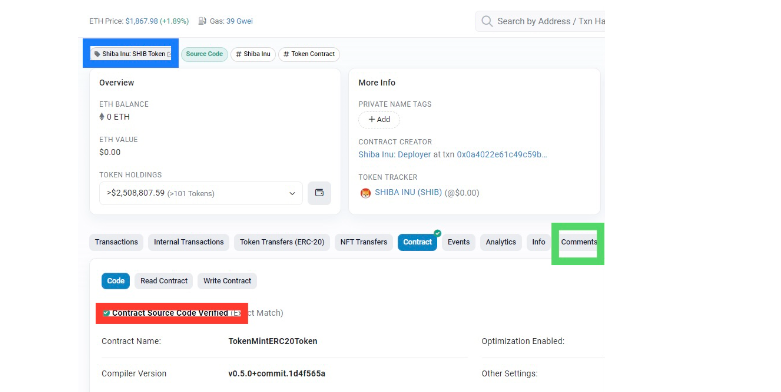
You can confirm if a smart contract is trustworthy by inputting its address on an appropriate block explorer. Most block explorers, like Etherscan.io, can tell if a contract’s source code (in red) is verified or not. In addition, you can check if the smart contract has a name (in blue).
It is important to note that the fact that a smart contract is unnamed does not necessarily imply that it is of malicious origin. At times, a project might be without a name because the smart contract is still in its early stages.
Furthermore, you can scroll through the comments section (in green) on the block explorer to see what users are actually saying about the smart contract. However, be extra vigilant in this section, as it could be easily manipulated by the fraudulent developers themselves.
4. Check Token on Coin Listing Sites
Smart contracts can represent a wide range of crypto-related projects or dApp functions, including tokens. However, not all tokens are as they appear on the surface.
For this reason, it is critical to conduct research on a smart contract-driven asset before using it; this is to avoid falling victim to phishing scams and other fraudulent activities.
You can visit a coin listing site, such as CoinGecko, to verify the genuineness of tokens defined or managed by smart contracts. These websites often contain all relevant information about the coin, such as the project’s address, socials, tokenomics, and so on.
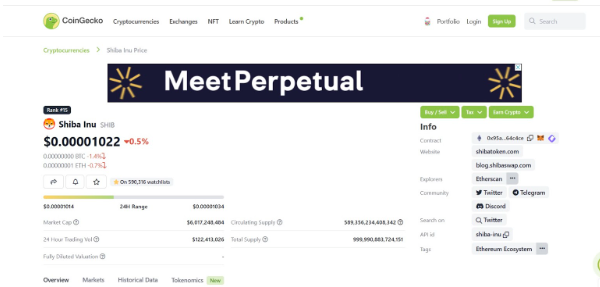
Also, a coin listing site will allow you to check whether a project has a real, active community that isn’t controlled by bots. Moreover, you can find the project’s white paper, which will help you investigate whether it isn’t just another crypto scam.
5. Analyze Recent Contract Activity
At times, it might not be enough to check if a project is available on a coin listing website or confirm the smart contract’s address on a block explorer. You should also endeavor to look through the recent transactions on the smart contract’s page on a block explorer.
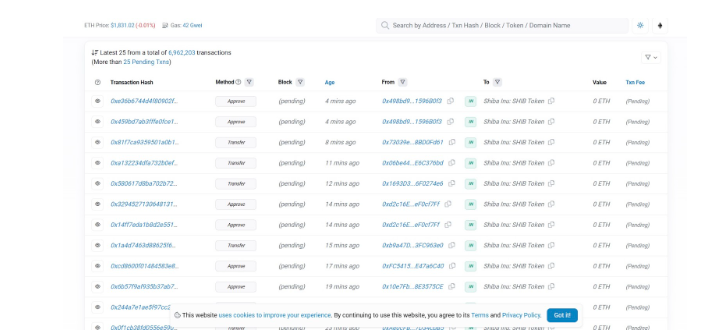
Indeed, perusing the transaction catalog of a smart contract can be quite tedious and overwhelming. But, you will find that it will help you spot unusual patterns and transactions. You will be able to discover any red flag that might cost later in the future.
For instance, a disturbing pattern to look out for on the block explorer is several buy and zero sell transactions. This is because most malicious projects prevent token buyers and holders from offloading their tokens when they want.
Final Thoughts
Web3 and blockchain technology have rapidly evolved in the past few years, with numerous lucrative and life-changing opportunities to show for its development. At the same time, these cutting-edge technologies have birthed new problems and inherent risks, including smart contract scams.
As a result, it is essential to prioritize your security when engaging in smart contract transactions and other crypto-related activities. From installing a security extension to doing your own research, there are several effective ways of protecting yourself when signing a smart contract.
As the owner of a self-custodial wallet, like Metamask, the responsibility of securing your assets lies with you. Fortunately, with the information in this article, you should find it easier to navigate smart contract transactions.
Also Read: Real World Assets On-Chain: What Are They & What Risks Do They Have?
[Editor’s Note: This article does not represent financial advice. Please do your research before investing.]
Featured Image Credit: ChainDebrief
This article was written by Opeyemi Sule and edited by Yusoff Kim