If you have ever used the Ethereum Network, you may have noticed the high gas fees and low throughput. This is due to how the blockchain verifies transactions ensuring immutability and decentralization which gave birth to sandwich attacks.
However, it also leaves room for MEV (Miner Extracted Value), with more than $630 Million extracted to date. In fact, users of decentralized exchanges (DEXs) often face a worse price thanks to such activities.
Here, we explore the way the Ethereum blockchain works, sandwich attacks – a form of MEV, and how to avoid them entirely.
Understanding MEV
To make sense of it all, we must first look at how Ethereum (and most L1s) process transactions.

Essentially,
- User signs a transaction within their wallet
- Transaction is relayed to a node
- Node verifies the transaction and adds it to its “mempool”, where the transaction is pending
- Miners validate the transaction and add it to a block
- If successful, the miner adds the block with the transaction to the blockchain
Mempool (memory pool) is a smaller database of unconfirmed or pending transactions which every node keeps. When a transaction is confirmed by being included in a block, it is removed from the mempool.
However, users can pay a higher gas fee for miners to place their transactions further up in the queue.
The problem is that pending transactions within the mempool are publicly viewable on Etherscan and is constantly being inspected by thousands of bots.
These bots then simulate the transactions and front-run them. This is done by performing the exact same transaction with higher gas fees, leaving the initial user with less or no profits.
What is a Sandwich Attacks
A bot can not only front-run but also back-run a transaction. Back-running is done after another user’s transaction, typically to perform arbitrage between DEXes or liquidations.
By combining the two methods, a bot can both front-run and back-run a transaction, effectively “sandwiching” it.
Essentially,
- User places a buy order of token X
- Bot sees this in the mempool and front-runs it, pushing the price up
- Causes high slippage and the user gets a worse fill
- Bot back-runs user, selling back tokens at a higher price
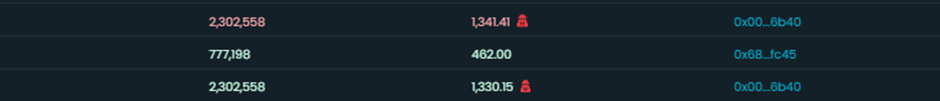
In practice, it looks like a simple buy and sell order from the same wallet, with a few extra $ETH in profit.
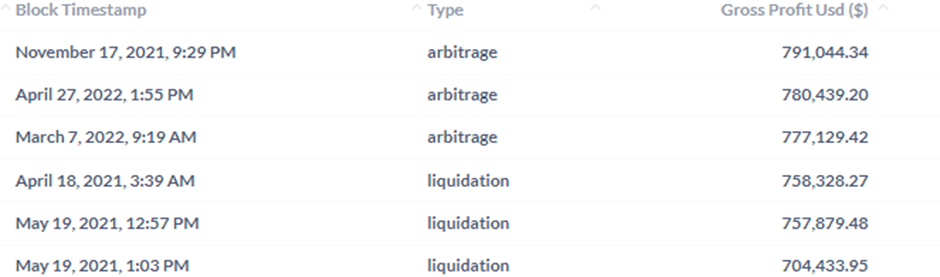
However, some of these sandwich attacks have resulted in thousands, if not millions of dollars in extracted value – sometimes in a single transaction. Furthermore, new ways of sandwiching transactions, such as “Just in Time” liquidity are becoming increasingly popular.
While you may think that sandwich bots would only target high-value transactions, you could not be further from the truth. Thanks to the currently low Ethereum fees, even a few hundred dollars in tokens can be susceptible to such attacks.
In fact, most MEV transactions only have double digit profits. Done hundreds of times, however, they stack up and actually “tax” the everyday user on routine transactions.
Avoiding Sandwich Attacks
The easiest way to prevent getting sandwiched is to place a limit order. Unlike typical market orders which are prone to slippage, users can set their fill price instead.

While this was typically only available on Centralized Exchanges, DEXs such as 1inch and Spiritswap currently allow this.
It lets users set predetermined swap prices on a multitude of networks, such as Ethereum, Avalanche, Arbitrium, and more. While this may incur some additional fees, it is especially worth it for larger swaps.
Announcing Flashbots Protect: a suite of tools that makes it easier to use Flashbots for frontrunning protection
— @bertcmiller⚡️🤖 (@bertcmiller) October 6, 2021
The first two Protect products are an API for developers and an RPC endpoint for end users
A brief thread about these productshttps://t.co/6HzIca4Qx6
Another way to protect your transactions is by using the Flashbots RPC. By sending transactions directly to miners, it bypasses the public mempool for additional protection.
While still in public beta, being able to protect against bots and not having to pay for failed transactions are just a few of its perks.
Closing Thoughts
While sandwich bots and MEV may be morally questionable, they no doubt speak to the transparency of Web3. However, methods to extract value are keeping abreast of security, such as time bandit and uncle block attacks.
As growing pains, new ways to protect against them are developing every day, though many are still unaware of this hidden tax on their transactions.
It is therefore important to continuously educate Web3 users, not only against bots, but also phishing, scams, and more. Furthermore, it may be time to question whether the trade-offs between decentralization and security are worth it.
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
Featured Image Credit: Chain Debrief
Also Read: Will The GameFi Bubble Explode? 3 Issues The Crypto Gaming Industry Have To Solve