Key Takeaways:
- 4 hacks in one day with Mango Market Manipulation on Solana losing over $100m
- This hack is not a flashloan attack
- Focus on security is essential for long-term web3 success
___________________________________________
Four hacks in a single day will go down in the history of web3 as being the greatest victory for hackers. Furthermore, the news of the SEC launching an investigation into BAYC creator Yuga Labs comes as no surprise in steering new users away.
Although at best a necessary evil, it is a painful journey towards a web3 future. While it may flake existing users out of the space, the technology remains. Maybe the bear market is here to humble us, in a way to focus on building a reliable and trustable system.
#Solana DeFi platform Mango has been hacked with over $100 million reportedly stolen.
— Watcher.Guru (@WatcherGuru) October 12, 2022
One of the latest hacks was on the DeFi platform on Solana, Mango Markets, which was exploited for over a $100 million.
Solana’s Mango market allows users to trade crypto for spot and trading perpetual futures. In addition to this, it is governed by the Mango DAO.
What actually went down?
@mangomarkets was just drained for over $100M. https://t.co/SI4hccCIQx
— OtterSec (@osec_io) October 11, 2022
🧵 pic.twitter.com/IAKyXgN8gM
OtterSec on Twitter explains clearly how Mango markets were drained.
Essentially, the attacker was able to manipulate their Mango collateral with a $5M USDC collateral and two accounts.

The hackers temporarily spike the collateral value, then took a large amount in loans from the Mango treasury.
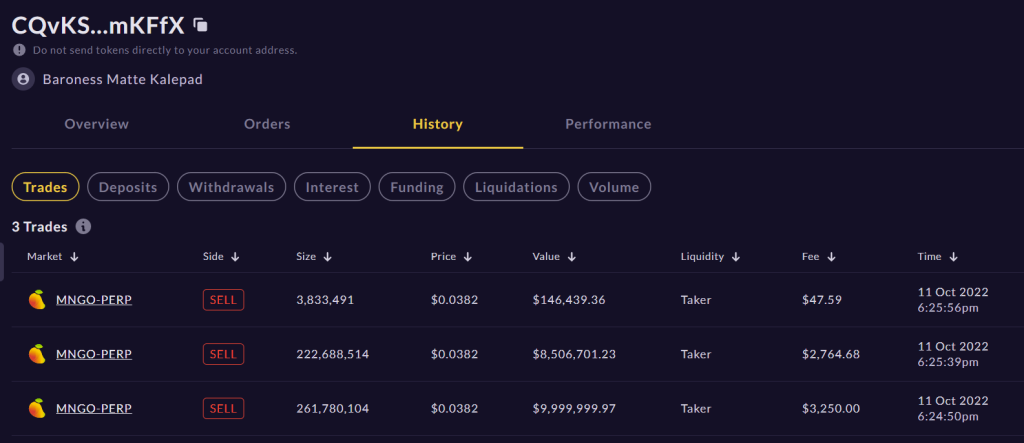
The $5M in USDC collateral was then used to buy 4.83M units of $MNGO perps, at a price of $0.0382 per unit.
The attack then moved the price of MNGO spot, it traded as high as $0.91.

With $0.91 per unit, account B was in the money by $483M * ($0.91 – $0.03298) = $423M.
With that amount in account B, it was enough to take a loan of $116M across a bunch of tokens, which effectively wiped out all available liquidity on Mango.

After the attack, MNGO/USD traded down to $0.02, which account A would profit from after shorting the $MNGO/USD pair with a $12M gain.
However, since there is no liquidity left to pay account A out, the attacker is left with the $116M he took from account B.
The SolanaFM team has tagged the hacker’s address on our explorer.
— Solana.FM🔮🔍 (@solanafm) October 12, 2022
We’re working closely with a few teams & individuals to find out more. https://t.co/4zTZaTNLi9 pic.twitter.com/cQSLBbU3L2
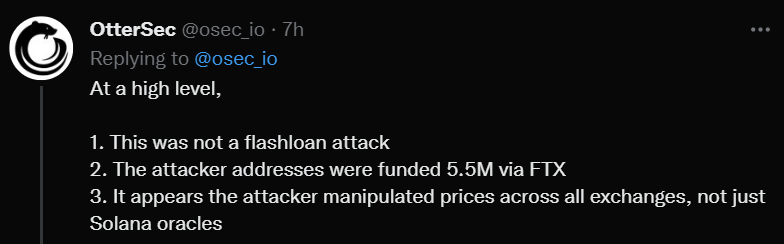
This was not a flash loan attack and not an issue with Solana Oracles, prices were directly manipulated on the exchanges themselves, and oracles simply reported the price as intended.
Also Read: Flash Loans in DeFi; How Do They Work and How to Capitalize on Them In Arbitrage?
This form of manipulation requires a starting amount of capital, $10M USDC, while some argue that this amount would have little impact on protocols, others say that the design of the 10x exploit opportunity mango offers is broken and likely to be exploited sooner or later.
Accounts involved with Mango Market hack
Our friend at SolanaFM, a block explorer which provides analytics and indexing services for Solana, @0xFA2, went into the details of the transfer and theorize and doubt the wallet is from a CEX, as they usually contain more than just USDC.
Also Read: SolanaFM Successfully Completes $6.3 Million Seed Round, Eyes Aptos and Sui For Expansion
The images below show transaction records between yUJw9 to 41zCU where 57,519,769.626603 USDC was transferred.
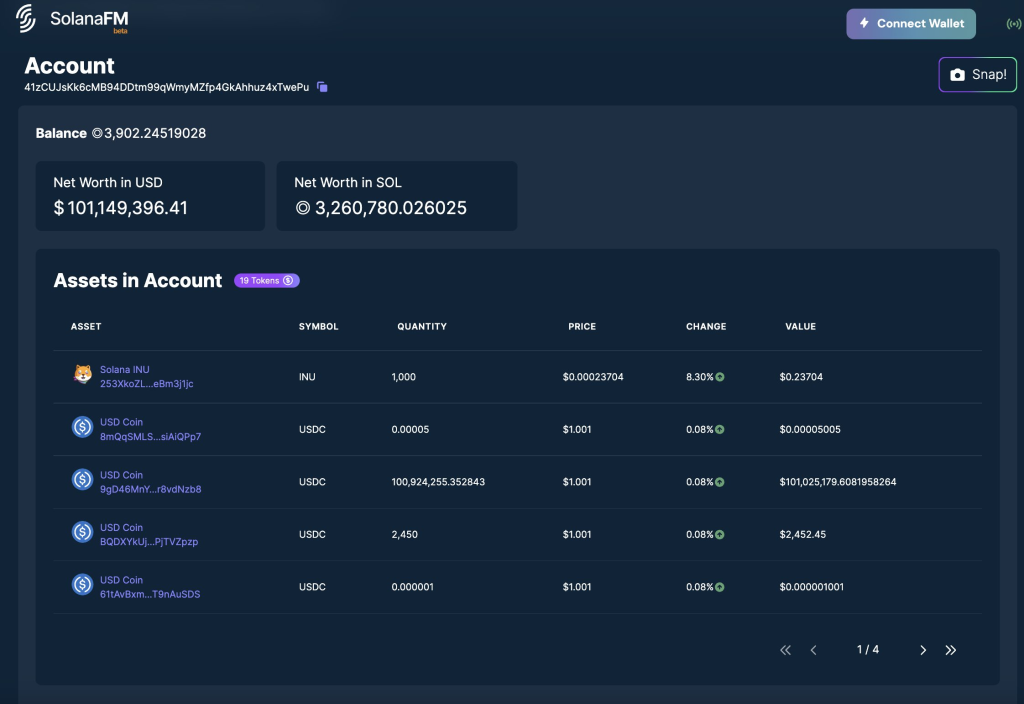
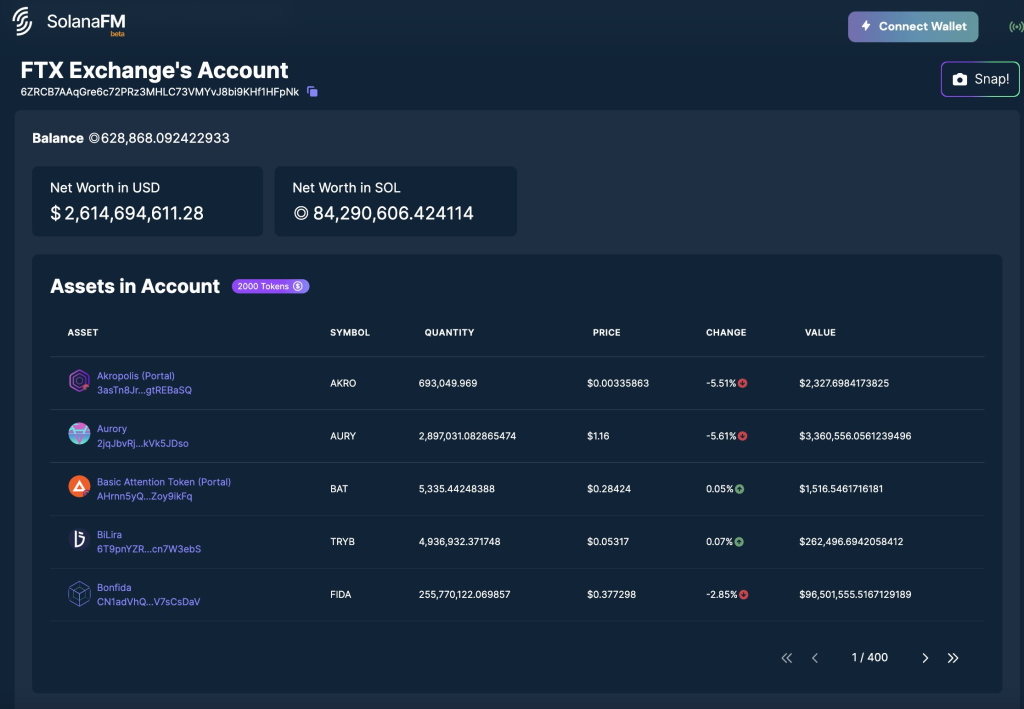
While the interaction between 41zCU to 7VHUF is interesting as their inflow and outflow interactions are directly involved with one another, the 7VHUF wallet actually owns the largest % of USDC on the Solana network.
While there may not be any conclusive evidence, as of the time of writing, this thread goes a little deeper into identifying potential stakeholders during this hack.
Looks like the Mango hacker had ~$57M USDC withdrawn to 41zCUJsKk6cMB94DDtm99qWmyMZfp4GkAhhuz4xTwePu
— Tristan ζ (@Tristan0x) October 12, 2022
This address has been around for a long time (1.5yrs+) and regularly sees 100s of millions in USDC go through it & #3 holder of USDC on Solana. Possibly @circlepay controlled? pic.twitter.com/zerlu8A2jj
If you guys want to go deeper, these are the address details you may need.
Hacker address: https://solana.fm/address/9BVcYqEQxyccuwznvxXqDkSJFavvTyheiTYk231T1A8S…
Withdraw address: https://solana.fm/address/41zCUJsKk6cMB94DDtm99qWmyMZfp4GkAhhuz4xTwePu?cluster=mainnet-qn1
Flagging of address
The SolanaFM team has tagged the hacker’s address on our explorer.
— Solana.FM🔮🔍 (@solanafm) October 12, 2022
We’re working closely with a few teams & individuals to find out more. https://t.co/4zTZaTNLi9 pic.twitter.com/cQSLBbU3L2
SolanaFM has flagged the exploiter’s address and tracked their wallet activity to see the movement of the funds.
OtterSec also cleared some misinformation on what went down with the Mango Markets hack.
The future of web3 security
In my opinion, for us to see mass adoption, there has to be a shift in focus in treating security, not like an event-based practice but a continuous process for improvement.
It should not be a “set of checkboxes to fill and set aside,” as the security world should not end after the discovery or audit. In many cases, as we heard before such as the Nomad bridge hack, exploits were based on mistakes from “post-audit upgrades.”
However, there is a growing trend in how the community is responding to hacks in being more organized and streamlined. Crypto twitter floods with contributors in the space eager to help, but lack of organization might get details lost in transition.
Diving deeper into the accounts involved in the Mango Markets hack.
— FA2 | SolanaFM (@0xFA2) October 12, 2022
While on-chain monitoring and social media as a platform detect active attacks quickly, the current security of crypto is limited in a reactive manner or a preventive one. The focus on this aspect of crypto is often overlooked, but essential to its long-term success.
Also Read: Maximizing Returns in Crypto: Understanding The 4 Phases of a Market Cycle
[Editor’s Note: This article does not represent financial advice. Please do your own research before investing.]
Featured Image Credit: Chain Debrief